Este sitio web utiliza cookies que permiten el funcionamiento y la prestación de los servicios ofrecidos en el mismo. Estas cookies y/o tecnologías similares que almacenan y recuperan información cuando navegas, realiza funciones tales como reconocerte cuando vuelves a nuestra web o ayudar a nuestro equipo a comprender qué secciones de la web encuentras más interesantes y útiles.
Information Security Policy and National Security Scheme
La Dirección de Future Space, consciente de la necesidad de promover, mantener y mejorar el enfoque hacia el cliente en todas sus actividades, ha
implantado un Sistema de Gestión Integrado (SGI) conforme al estándar cuyo objetivo final es asegurar que entendemos y compartimos las
necesidades y metas de nuestros clientes, intentando prestar servicios que cumplan sus expectativas trabajando en la mejora continua. Manifiesta
expresamente su compromiso de potenciar la Seguridad y Ciberseguridad de la Información del servicio prestado, y se compromete a satisfacer las
necesidades y expectativas de las partes interesadas, a mantener alta nuestra competitividad en los servicios y productos de Data & Analytics,
Ciberinteligencia, Internet of things, Cloud empresarial y Desarrollo de aplicaciones
Mission and Objectives:
- Encourage continuous improvement of services and customer support.
- Continue positioning Future Space as a reference in the sector.
- Providing software solutions to transform data and information to aid in decision making for our clients.
- To provide clients with the most professional equipment and to have highly qualified technicians, experts in the required disciplines and accustomed to working as a team, available immediately and for as long as necessary.
- Tener una prestación del servicio basada en nuestro compromiso con la mejora continua de nuestros sistemas, con la seguridad y ciberseguridad de la información como pilar central y por defecto.
Our mission and objectives will be achieved through:
- Un sistema de objetivos, métricas e indicadores de mejora continua, seguimiento, medición de nuestros procesos internos, así como de la satisfacción de nuestros clientes. Estableciendo y supervisando el cumplimiento de los requisitos contractuales para asegurar un servicio eficaz y seguro.
- Formando y concienciando continuamente a nuestro equipo para tener el mayor grado de profesionalidad y especialización posible, además teniendo nuestras infraestructuras en un estado adecuado y en concordancia con los requerimientos de nuestros clientes.
- With a secure product procurement management procedure.
- Complying with the requirements of current legislation, especially with the GDPR and compliance with our Security Documentation.
- Introducing continuous improvement processes that allow a permanent advance in our Information Security management.
- Gestionando y elaborando planes para la gestión y tratamiento de los riesgos con una metodología de análisis y gestión de riesgos utilizada, basada en ISO 31000.
- Managing internal and external communications and information stored and in transit.
- Ensuring interconnection with other information systems.
- Managing and monitoring activity with log management.
- With special attention to the management of security incidents.
- Ensuring the continuity and availability of the business and services.
- Asegurar que nuestros Activos y Servicios cumplen con las medidas del ENS de Nivel ALTO para las dimensiones de Confidencialidad, Integridad, Disponibilidad, Autenticidad y Trazabilidad.
Likewise, these principles should be considered in the following safety areas:
- Física: Comprendiendo la seguridad de las dependencias, instalaciones, sistemas hardware, soportes y cualquier activo de naturaleza física que trate o pueda tratar información,, así como los accesos físicos.
- Lógica: Incluyendo los aspectos de protección de aplicaciones, redes, comunicación electrónica, sistemas informáticos y con los accesos lógicos.
- Político-corporativa: Formada por los aspectos de seguridad relativos a la propia organización, a las normas internas, regulaciones y normativa legal.
El objetivo último de la seguridad de la información es asegurar que una organización pueda cumplir sus objetivos utilizando sistemas de información. En las decisiones en materia de seguridad deberán tenerse en cuenta los siguientes principios básicos:
- Organización e implantación del proceso de seguridad.
- Análisis y gestión de los riesgos.
- Gestión de personal
- Profesionalidad.
- Autorización y control de los accesos..
- Protección de las instalaciones.
- Adquisición de productos de seguridad y contratación de servicios de seguridad.
- Mínimo privilegio.
- Integridad y actualización del sistema.
- Protección de la información almacenada y en tránsito.
- Prevención ante otros sistemas de información interconectados.
- Registro de la actividad y detección de código dañino.
- Incidentes de seguridad.
- Continuidad de la actividad.
- Mejora continua del proceso de seguridad.
Security roles or functions
Responsible for the information:
Determine the requirements of the information processed.
- To implement and maintain the Integrated Management System (IMS), continuously improving its effectiveness.
- Implement and maintain the ENS by continuously improving its effectiveness.
- Supervise procedures and technical instructions.
- Implement the measures and follow-ups indicated by the DPO.
- Follow up and verify the implementation and effectiveness of all established corrective and preventive actions.
- Ensure that the implemented system complies with the established standard.
- Analyze the data obtained in the Integrated Management System (IMS) and ENS and propose improvements.
- Draw up the annual internal audit plan.
- Participate in management review decision making.
- Management of safety non-conformities.
- Participate in External Audits.
- Responsible for the company's private data in terms of loss, theft and outdatedness.
- Comply with the manual of good information security practices.
- Delivers training programmes so that staff know how to act in the event of a contingency.
- Maintain updated means of contact with the authorities.
- It keeps the inventory of media containing personal data.
- Analyzes the audit reports and submits the conclusions to the data controller.
- Convene the ISC meetings.
- Generates ISC meeting minutes.
- Manages IS non-conformities, corrective actions and preventive actions.
- Maintains IMS documents.
- Maintains and deploys the security policy of Future Space as well as the rest of the policies to the staff involved in each of them.
- Responsible for the management of the security audit of data protection and GDPR.
- Supervises the LOPD tasks of the DPO.
- It prepares the security documents of Future Space.
- Draw up agreements for the processing of data by third parties.
- Attends to incidents in the field of data protection.
- It is responsible for contacting the authorities if necessary.
- Aplicación y supervisión del cumplimiento de las políticas del SGI.
- Mantenimiento y aplicación del Documento de Aplicabilidad del SGI.
Systems Manager:
Determines the requirements of the services provided.
- Develop, operate and maintain the System throughout its life cycle, from its specifications, installation and verification of its correct functioning.
- Define the topology and management policy of the System, establishing the criteria of use and the services available in it.
- Define the policy of connection or disconnection of equipment and new users in the system.
- Approve changes that affect the security of the System's mode of operation.
- Decide on the security measures to be applied by the System component suppliers during the development, installation and testing stages of the System.
- Implement and control the specific security measures of the system and ensure that they are properly integrated within the general security framework.
- Determine the authorized hardware and software configuration to be used in the system.
- Approve any substantial modification to the configuration of any element of the System.
- Carry out the mandatory risk analysis and management process in the System.
- Determine the category of the system according to the procedure described in Annex I of the ENS and determine the security measures to be applied as described in Annex II of the ENS.
- Elaborate and approve the security documentation of the System.
- Delimit the responsibilities of each entity involved in the maintenance, operation, implementation and supervision of the System.
- Ensuring compliance with IHR obligations
- Investigate security incidents affecting the system and, if necessary, notify the Head of Security or whoever he/she may determine.
- Establecer planes de contingencia y emergencia, llevando a cabo frecuentes ejercicios para que el personal se familiarice con ellos.
- Además, el responsable del sistema puede acordar la suspensión del manejo de una cierta información o la prestación de un cierto servicio si es informado de deficiencias graves de seguridad que pudieran afectar a la satisfacción de los requisitos establecidos. Esta decisión debe ser acordada con los responsables de la información afectada, del servicio afectado y el responsable de seguridad, antes de ser ejecutada.
Information Security Manager:
Determines decisions to meet information security and service requirements.
- Responsible for cybersecurity.
- Supervise the Safety Manual, procedures and technical instructions.
- Overall responsibility for managing the implementation of security practices.
- Ensure that the implemented system complies with the established standard.
- Analyze the data obtained in the Information Security Management System and ENS and propose improvements.
- Participate in management review decision making.
- Participate in External Audits.
- Responsible for the risk of physical intrusion of the company's devices.
- Comply with the manual of good information security practices.
- Segregation of tasks and environments.
- Report any fire, flood or HVAC emergency that may activate the BCP.
- Review the Business Continuity Plan.
- Verifies the functioning of the Business Continuity Plan.
- Controls the access of people to the premises where the systems are installed.
- Supervises the security incidents that occur.
- Performs and safeguards backups.
- Generates risk management treatment plans and monitors their implementation.
- Update the risk analysis.
- Oversees the collection of metrics.
- Performs IMS security reviews.
- Maintains the Business Continuity Plan.
- Incorporates corrective measures in the incident log.
- Enforcement and monitoring of compliance with SGI policies.
Responsible for the Service:
Determines the security levels of the services.
- Ensure compliance with the objectives and metrics established for the service (SLAs).
- Daily organization of resources.
- Responsible for the loss and theft of information of services and IT solutions for clients and users in general.
- Comply with the manual of good practices.
- Determines the requirements of the services provided.
- Program, direct, coordinate, supervise and control all the activities of the service.
- Review and compliance of service reports.
Information Security Committee
The Information Security Committee (ISC) of Future Space reaches the entire company, is the mechanism for coordination and conflict resolution, among other functions:
- Appointment and/or renewal of security positions, as well as their roles and responsibilities.
- Create, plan, implement and integrate the strategic direction of the organization and align it with the ISMS.
- Knowledge of the ICT market and new technologies and their application in the company.
- Management and supervision of the different security projects of the company.
- Participate in and promote compliance with the organization's information security policy.
- Ensure compliance with legal provisions and regulations of public administrations and internal rules relating to information security.
- Approval of the ISMS, as well as its changes and new versions.
The ISC is composed of: Chairman, Vice-Chairman, Chief Information Officer, Service Manager and Information Security Officer.
Estructuración de la documentación de seguridad del sistema:
La documentación del sistema sigue la siguiente estructura:
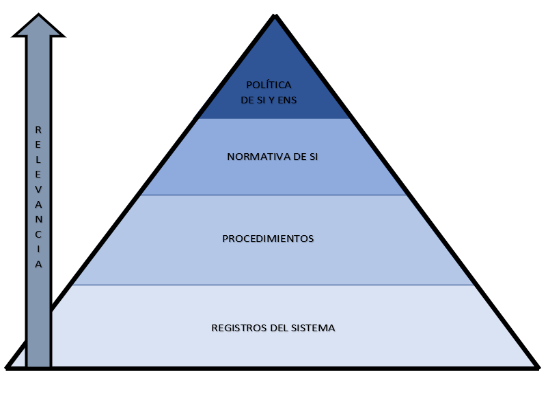
La clasificación de la información del sistema se clasifica en las siguientes categorías, tal y como se establece en el procedimiento PS.8 Gestión de activos
FutureSpace v1:
- Uso Público
- Uso Interno
- Uso Confidencial
Legislación aplicable en materia de tratamiento de datos de carácter personal
En materia de tratamiento de datos de carácter personal se tendrá en cuenta, principalmente, el Reglamento (UE) 2016/679 del Parlamento Europeo y del Consejo, de 27 de abril de 2016, relativo a la protección de las personas físicas en lo que respecta al tratamiento de datos personales y a la libre circulación de estos datos y por el que se deroga la Directiva 95/46/CE y la legislación nacional correspondiente.
El marco legal y regulatorio aplicable se encuentran recogido en el documento Registro Identificación y evaluación de requisitos legales Future Space
Los riesgos que se derivan del tratamiento de los datos personales se analizan en el documento Gestión de Riesgos de Privacidad de LOPD
Considerando estas pautas, esta dirección reitera su más firme compromiso aunando esfuerzos para el logro de estos objetivos, por lo que esta política
es entendida, implantada y tenida al día en todos los niveles de la organización.
Considering these guidelines, this management reiterates its firm commitment to join efforts to achieve these objectives, so that this policy is understood, implemented and kept up to date at all levels of the organization.
Fdo: Almerino Furlan
Presidente
Presidente
MARCO LEGAL: Real Decreto 311/2022 de 3 de mayo, de modificación del Real Decreto 3/2010, de 8 de enero, por el que se regula el Esquema Nacional de
Seguridad en el ámbito de la Administración Electrónica.
Revisión 2 – Fecha: 22/03/2023

