OSINT for researching people on the Internet
Today and every minute that passes, millions of data are recorded and uploaded to the network, whether on the Internet, Deep Web or Dark Web. Data hosting is such that it is estimated that, on average, each person maintains a Digital Footprint of almost 6 Gb of information on the net. This information, despite what one might think, is available, open and declassified to be exploited by analysts through what we call Open Source Intelligence( OSINT).
Among the sources of information that are handled when performing an intelligence analysis process, OSINT sources are taking a lot of weight. This is due to the amount of possibilities they offer, the quick and easy access, and above all the enormous range of OSINT tools. Many of them are even free and have been developed to treat the information obtained and give it added value to turn it into intelligence.
For this reason, one of the biggest dangers that exist today is not being aware of the information about us that wanders around the web. We are not only talking about the information that is dumped externally (official bulletins, public administration records, university directories, web page records, cookies, servers, etc.), but precisely the information that we ourselves share, in this case on social networks.
What information can be extracted from social networks with OSINT?
Everyone knows that the use of Facebook, Twitter, Instagram or LinkedIn is not the same. This is precisely what helps profile the person behind such social networking accounts.
If the person is prone to have profiles in all or some of them, with their level of activity we could get to know where they live, where they have traveled or what their interests are. Furthermore, we may even be able to find out where someone is from and know their family just by the amount of use they make of their Facebook profile.
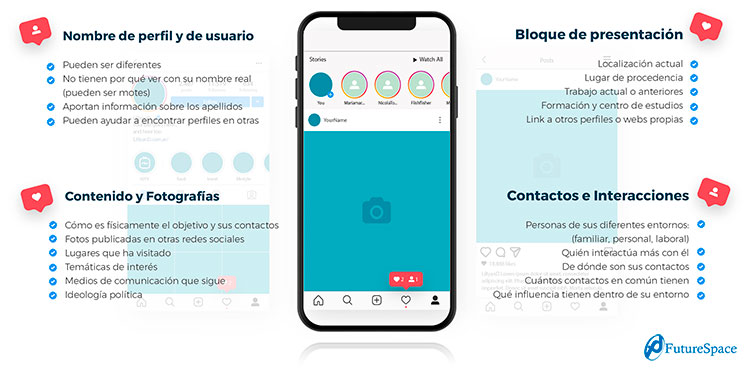
Responsible fingerprinting: using social networks safely
As you can see, there is a lot of data that can be extracted from social networks, and although most networks provide the user with privacy options, these are not always effective.
The interesting thing is that most people in these cases imagine that to get this information they need hackers in dark rooms, phishing operations or big information thefts like the case of Cambridge Analytica's Facebook. But nothing could be further from the truth. You don't have to go on such a large scale or for illicit purposes.

The Fingerprint of hundreds of people is investigated daily for Human Resources processes. This is done to profile your exposure perimeter in open sources or simply to watch that nobody does a smear campaign against your company.
Companies like Future Space do this by using only the information that we ourselves publish daily on social networks. Many in this situation decide to close their profiles and remove all their content. On the other hand, and taking into account that removing all this information completely is an almost impossible task for many, it is much more useful to learn how to use social networks.
Today, there are many people whose work depends on social networks and they cannot afford to do without them. Knowing what content to post, who to connect with, what information to reflect and what to keep private will help us enjoy them with less risk of exposure.