Cybercriminals continue to innovate and try to deceive the user in multiple ways due to the dangers of the Internet. Their motivations are varied, but the main one is financial gain. To achieve this, they use different techniques. Below, we review some of them that you should know:
What is Vishing and how does it work?
Vishing attacks are similar to the well-known phishing attacks but using phone calls. Victims receive fraudulent phone calls where the attacker poses as someone else: IT support, financial institution, telephone operator, public body... This call is used to extract personal information from the victim in order to carry out other attacks.
Cybercriminals may register domains and create phishing pages, duplicating a company's internal login page.
Attackers collect information about company employees. These employee profiles can be in public HR profiles, marketing or HR tools, as well as any other public data.
By using this information and knowledge they manage to gain the trust of the users. They can send them a link or a request where they enter their username, including two-factor authentication (2FA), and one-time passwords (OTP). This, they will then use to gain access to the company's systems.
What is Smishing and how does it work?
Another variant we can find is the technique known as Smishing, which consists of sending text messages (SMS) to mobile phones. The messages try to make the user visit a fraudulent website in order to obtain the user's credentials or other personal information. However, it could also have other purposes such as infecting the device.
Passwords
New information readings from different services such as Dropbox, Xiaomi, Adobe, etc., are frequently added. These contain user account information such as email, username and password that are made public and will be used by cybercriminals to try to get into different services. Therefore, if the user has reused the same password for several sites, it is easy for the rest of their accounts to be compromised as well.
Reusing the same password is especially serious, when we use it indiscriminately in the private and public sphere. For example, putting the key to our business email in our Linkedin account.
On the following website it is possible to check via our email if our personal data has been published due to information leaks from different services: https://haveibeenpwned.com/
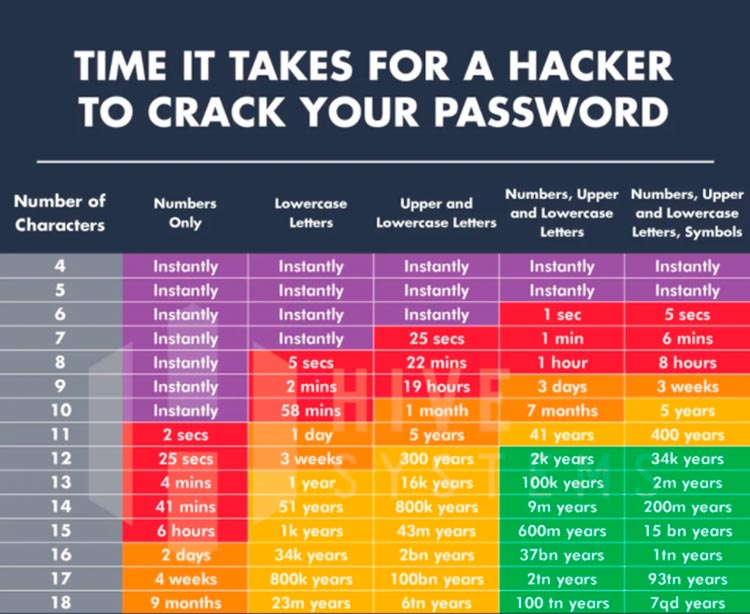
On the other hand, if we use a weak password it will be easy for an attacker to use brute force to gain access to our account.
Ideally, a strong password should be used for each service with alphanumeric characters combining uppercase, lowercase and special characters. Such a password is impossible for us to remember. Therefore, we will use a password manager like KeePass, which will allow us to store passwords securely.
Apart from having a secure password, it is very important to activate the two-step verification (2FA) whenever the service allows us to do so. This way, if for some reason an attacker has obtained our password, he will also need the 2FA code to be able to access.
Conclusion
Finally, we have seen that most of them are common sense practices. We must always remember, verify and distrust those who ask for our data and passwords. It does not matter if it is from an email, a web (phishing), by phone (vishing) or by SMS (smishing). We must also remember to have a strong password and a second factor activated. By applying these practices we will achieve a safer teleworking environment.












